Cyber Threats on DNS Servers
Overview of DNS
The Domain Name System (DNS) is a foundation protocol of hierarchical and decentralised naming system commonly used on the Internet to resolve human-readable domain names into numeric Internet Protocol (IP) addresses. The original designed DNS protocol (RFC 882 and RFC 883) was published by Internet Engineering Task Force (IETF) in 1983. DNS includes a data repository to store domain names and their associated IP addresses, and acts like a directory or phone book of the Internet. The function of mapping domain names to IP addresses is called “Name Resolution”. The protocol that DNS uses to perform the name resolution is called the DNS protocol. However, the DNS specification does not have any mechanism to secure the authenticity and privacy of DNS transactions, that may cause DNS data interception and modification during the transmission process.
The process which DNS utilises to turn Uniform Resource Locators (URLs) into routable IP addresses encompasses six main steps. “https://www.example.com/index.html” will be used as an example to explore the process in the following diagram:
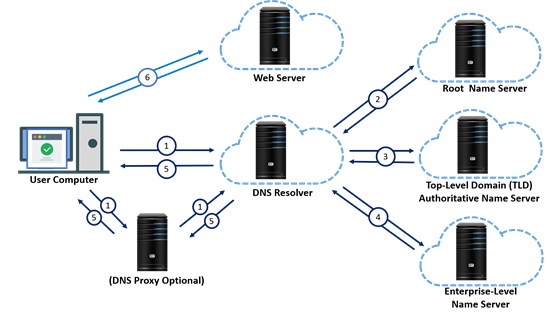
The DNS resolver forwards the DNS query to a root name server that returns an IP address of the corresponding top-level domain (TLD) name server, i.e. “.com” name server.
The DNS resolver directs the DNS query to the appropriate TLD name server that returns an IP address of the corresponding Enterprise-Level name server, i.e. “example.com” name server.
The DNS resolver forwards the DNS query to the Enterprise-Level name server that returns an IP address of the corresponding web server, i.e. “www.example.com”.
The DNS resolver returns the web server IP address to the web browser, and adds that response to its cache. Next time when that address needs to be resolved, the result is taken from the cache instead of making another DNS request.
The web browser connects to the web server and displays its webpage to the user, i.e. “https://www.example.com/index.html”.
According to a number of cyber security threat reports, DNS-based attacks are becoming highly sophisticated and volumetric. Attackers are increasingly adopting multifaceted techniques to exploit different DNS components such as recursive resolvers and authoritative DNS servers. Besides, data exfiltration via DNS-based covert channels often goes undetected over legitimate DNS traffic. The increasing difficulties to detect and mitigate the attacks make securing DNS infrastructure even more crucial to keep DNS secure and resilient. The impact caused by DNS-based attacks is profound due to its mission-critical role. The consequences of not securing DNS may result in a higher risk of data breach, service downtime, compliance failure and compromised reputation of an organisation.
DNS hijacking (also called “DNS Redirection”) is a type of DNS attack in which DNS queries are manipulated to redirect users to malicious sites. DNS hijacking can be used for pharming or phishing by taking over users’ DNS requests. There are five common types of hijacking attacks:
Also known as DNS spoofing, DNS cache poisoning is a DNS cache attack that attackers insert fraudulent data into the cache of a DNS resolver. The DNS resolver makes use of the cache for storing processing results of DNS queries to enhance performance when receiving the same query. The fraudulent data will redirect users to malicious sites.
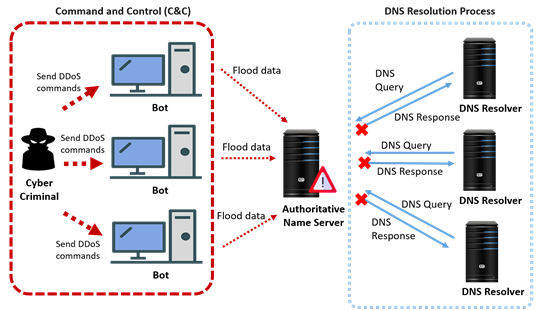
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal DNS traffic of a targeted DNS server with a flood of Internet traffic. Successful launching of a DDoS attack on DNS will hamper the resolution of domain into IP addresses of the zone and its sub-zones, rendering other services inaccessible and causing even more catastrophic results. Two main attack techniques exist for DDoS attacks – amplification and reflection. They are often used together to maximise the impact on the target.
The record for the largest DDoS attack ever recorded was of 2.3 Tbps, mitigated by Amazon Web Services (AWS) Shield service in February 2020. The attack was carried out using hijacked Connection-less Lightweight Directory Access Protocol (CLDAP) web servers to reach massive DDoS bandwidths. In 2016, a series of DDoS attacks on a DNS service provider, Dyn, was launched, which caused major Internet platforms and services unavailable to many users in Europe and North America.
Attackers flood DNS queries to DNS servers in an attempt to exhaust DNS infrastructure and server resources of a particular domain name space. By disrupting the DNS name resolution capability, the flood attack will compromise websites’ or online business applications’ ability to respond to legitimate transaction traffic. DNS flood attacks can be difficult to distinguish from normal heavy traffic because the large volume of traffic often comes from a multitude of unique locations, querying for real records on the domain, mimicking legitimate traffic.
PRSD attack (also called “Water Torture Attack”, or NXDOMAIN Flood Attack) is another type of DDoS attack that attackers send a large number of queries for random, non-existent subdomains of legitimate domains. The attack intends to exhaust server resources and take down the authoritative name servers for targeted legitimate domains.
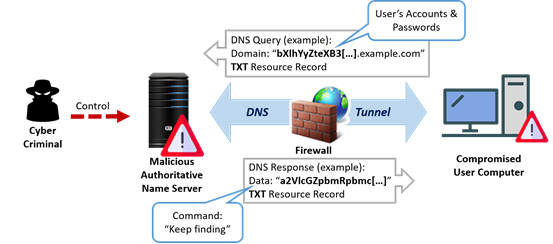
DNS tunneling refers to the control of the domain name and DNS server to encode data inside DNS queries and responses to communicate with the controlled/compromised DNS server and user computer. DNS tunneling attack leverages normal outbound DNS requests to the attacker’s server, providing attackers a covert command and control channel, and a data exfiltration path by Command and Control (C&C) method. Compromised data is encoded into several DNS host queries over time, allowing for the gradual exfiltration of sensitive data.
Domain name squatting (also called Cybersquatting) is a type of DNS threat that attackers squat domain names to redirect users to malicious websites. Organisations may miss renewal dates on their domain names and the domain squatter takes advantage of the domain names to present a high risk to users visiting them. Squatting domains are often used or repurposed for attacks. For example, attackers can use squatting domains to distribute malware or to conduct scams and phishing campaigns.
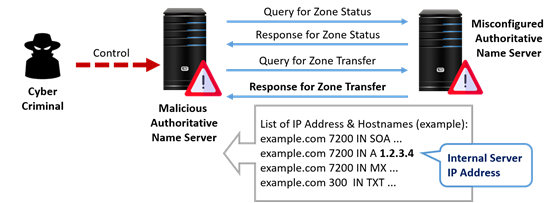
DNS zone transfer is a network mechanism for copying the contents of the zone file on a primary DNS server to a secondary DNS server. Without proper configuration of the authorised secondary DNS server transfer, attackers can replicate the internal IP addresses, servers and other information of an organisation from exposed DNS database (e.g. private domain records, SPF TXT records) through DNS zone transfer attack. Attackers can understand the network topology then deliberately exploit the information and infrastructure systems of an organisation.
Organisation can implement the following preventive measures to prevent threats and attacks on DNS:
In the event of a DNS attack, the organisation should consider taking the following actions to effectively respond to and contain the incident:
Domain Name System Security Extensions (DNSSEC) enhances the security level by validating DNS data of a domain name during the IP address lookup. It uses cryptographic signatures to confirm the DNS data received is genuine. DNSSEC helps ensure data integrity and authenticate the origin of DNS data, and thus helps prevent attackers from redirecting users (at DNS level) to fake websites. However, it should be noted that the domain should be DNSSEC-enabled and the DNS resolver should be DNSSEC-aware in order to provide the protection.
DNSSEC-Enabled Name Resolution Workflow
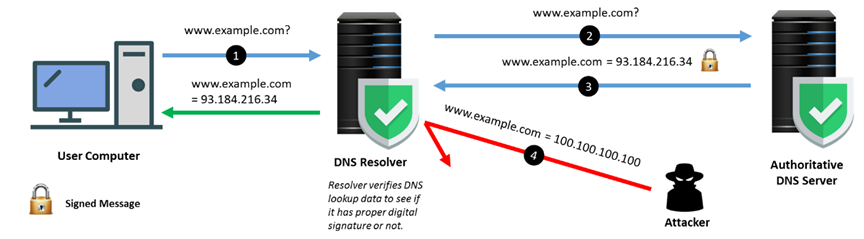
DNS Filtering is a technique of blocking access to certain websites, webpages, and IP addresses. DNS filtering solution filters domain names/IP addresses known to be malicious and reduces the risk of infection when a user attempts to access malicious sites. It can be implemented by DNS Blacklist and DNS Sinkhole. The DNS Blacklist provides automated, real-time checking of DNS queries against a list of malicious IP addresses. The DNS Sinkhole is configured to forge a response to a DNS-query for the known malicious domains (from the DNS Blacklist), resolving it to a definable but fake IP address to the client. If the client tries to access the fake IP address and there is a security rule in place, access to the malicious domain can then be blocked.
WHOIS is a query and response protocol that provides information on domain names and IP address blocks from a database. It stores and delivers database content in a human-readable format. The Internet Corporation for Assigned Names and Numbers (ICANN) currently requires the e-mail addresses, phone numbers, and even mailing addresses of all owners and administrators of domains to be publicly available.
To protect information of domain name registrants and administrators being demanded to be made public on WHOIS directories, there are domain privacy protection services available from domain name registrars which essentially masks domain contact information to protect the privacy of domain name registrants.
Disclaimer: Users are also recommended to observe the disclaimer of this website and read the user agreements and privacy policies of the security software and tools before downloading and using them.
