Data Breach
Data breach is a security incident in which data are accessed, altered, erased, stolen or leaked from a system without the consent of the system’s owner. The victims of a data breach range from individuals to organisations and governments and the data breached could be personal information, personally identifiable information (PII), medical records, trade secrets, financial information, etc. Data breach can be caused by cyber attacks, malicious acts of insiders, negligent acts of employees, loss or theft of devices and documents, etc. Such data breaches can lead to serious impacts on affected individuals or organisations, including identity theft, financial loss, reputation damage, legal liability, etc. Most of the time, cyber criminals try to monetise the attack and use the stolen data for identity theft or other fraudulent purposes.
Recent trend of data breach
The rise in data breaches is evident and alarming. According to a global data breach security report by a non-profit making security organisation in 2021, the overall number of data breach increased by more than 68% compared to 2020. The report reveals that the three primary causes of a data breach are cyber attacks (86%) (including phishing and malware attacks), human and system errors (9%) (including misconfiguration and loss of devices) and physical attacks (2%) (including document or device theft). Healthcare, financial service, manufacturing & utilities, professional service and technology sectors are at the forefront of the data compromise; and they account for more than half of the breaches in 2021.
Data protection laws
In recent years, law enforcements and related departments / agencies in some jurisdictions have tightened regulations governing the personal data protection and cross-border data transfer. Data Protection Regulation (GDPR) came into force since 2018 in the European Union, California Consumer Privacy Act (CCPA) came into force since 2018 in some areas in the United States of America and Personal Information Protection Law (PIPL) came into force since 2021 in the People’s Republic of China. To combat the rising trends of data breaches, GDPR and some other countries’ laws have also included stringent data breach notification rules to set out mandatory data breach notification requirement for organisations to inform both the competent authorities and the relevant individuals.
Although security tools may protect against most types of attacks, it is crucial to know the warning signs of a compromised system. Some of the major indicators are described below:

Figure 1: Signs of data breach
To minimise the risks of data breach, it is important to understand the major causes of data breach. The causes can be categorised into three common groups:
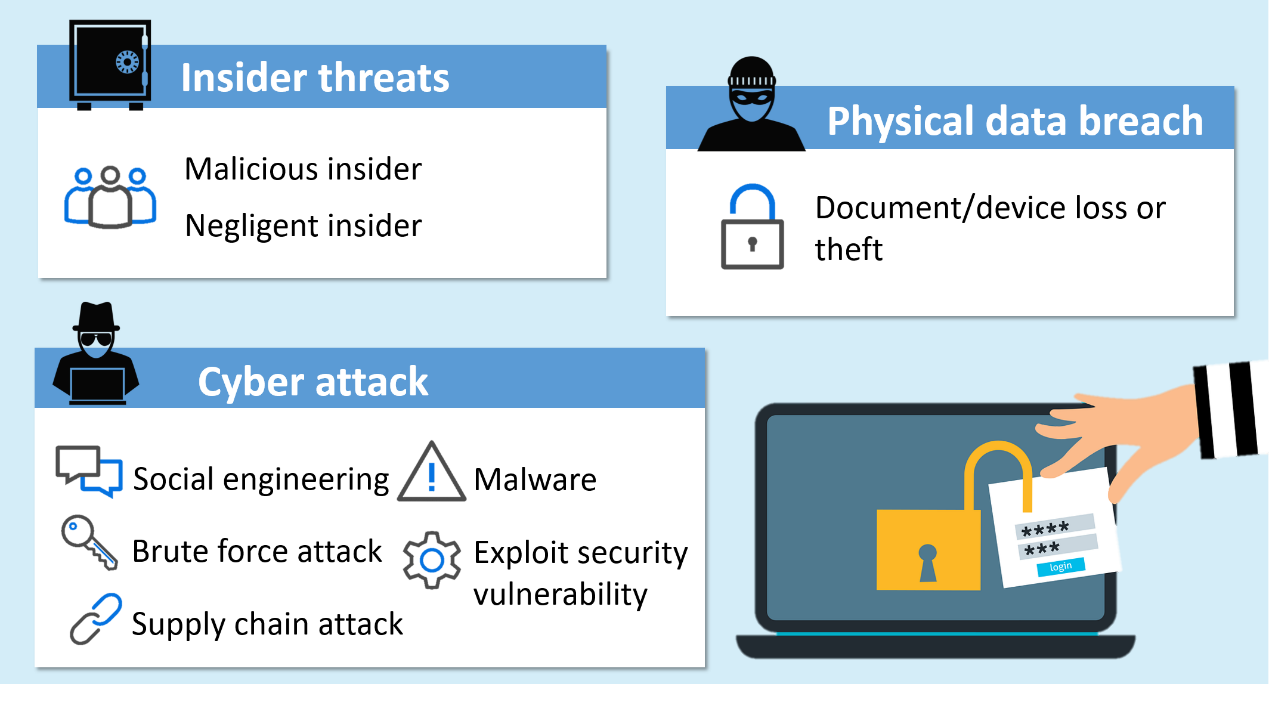
Figure 2: Common causes of data breach
An insider threat typically refers to potential attacks from users with legitimate access to organisations’ data, network or computer systems. Threat actors include employees, contractors or third-party vendors, etc. Insiders vary in their motivation and intent.
Example: In 2019, two employees of an energy company pleaded guilty to steal trade secrets from the company with intention to gain business advantage to start a rival company. More than 8 000 files containing sensitive information were leaked from 2011 to 2012.
Example: In 2021, a motor vehicle manufacturer reported a data breach by an unauthorised third party. Owing to an electronic file left unsecured by its marketing vendor, over 3.3 million customers’ data was leaked.
Cyber attack allows attackers to gain unauthorised access to organisations’ network or computer systems and steal the sensitive or confidential data. Attackers often infiltrate to gain access to protected information through the following stages and attack vectors:
Data breach caused by cyber attacks usually contains three main stages, including reconnaissance, attack and data exfiltration.

Figure 3: Data breach stages
Example: In 2020, a social media platform’s employees leaked user credentials due to spear phishing attacks. With the compromised accounts, attackers gained access to 130 famous private and corporate accounts and used 45 of these accounts to promote a Bitcoin scam.
Example: In 2021, a telecommunication company had fallen victim to a massive data breach. The attacker used brute force attack to breach IT servers and stole the personal information for more than 54 million customers.
Example: In 2020, threat actors infiltrated the supply chain of an information technology firm through injecting malicious code into the company’s software system update that automatically pushed out. Over 18 000 of its customers installed the updates and left them vulnerable to attack.
Example: In 2021, an oil pipeline company suffered a ransomware attack that shut down operations and cut off fuel supplies to millions of individuals. Nearly 100 gigabytes of data was stolen from the company servers for which ransom payment was demanded.
Example: In 2021, a cashless parking app had been breached due to a security vulnerability introduced by a third party vendor. Critical customer data of 21 million customers were leaked and sold on the dark web.
Sensitive documents or devices with sensitive data (e.g. USB storage device, hard disk, laptop) which are not physically secured, such as those left unattended in public places or sensitive data stored on portable devices without encryption, can cause a massive data breach.
Data breach can cause far-reaching and damaging consequences to organisation and individual. Depending on the extent of the data breach, it is possible that society and citizens can be threatened. The leakage of confidential information on asset, health and identity record can result in social panic and threats to personal safety.


Figure 5: General recommendation for preventing data breach
Best practices for organisations

Figure 6: Best practices for organisations to prevent data breach

Figure 7: Zero-trust architecture workflow
- Define the critical and valuable data or assets and enforce policy that ensures secure access to defined data or assets (refer to “Identify” section);
- Segment granular and secure subnetworks to allow easier dissection and building more specific security controls based on user and device identification; and
- Strengthen identity and access management to authenticate and authorise data points only the resources and services it needs.

Figure 8: Respond to data breach
Depending on the causes identified in early stage, containment measures may include:
- Improve the handling process of sensitive data;
- Review and revise access rights to sensitive data;
- Assess the adequacy of protection against unauthorised access to sensitive data and implement further security measures if necessary; and
- Strengthen the monitoring mechanism of data processing and detection effectiveness of early signs in data breach.
Disclaimer: Users are also recommended to observe the disclaimer of this website and read the user agreements and privacy policies of the security software and tools before download and use them.
